The Most Difficult CMMC Requirements
The 10 Most Difficult CMMC Requirements Explained
In the evolving landscape of cybersecurity, achieving CMMC (Cybersecurity Maturity Model Certification) compliance is foundational for organizations handling sensitive government data. For many, however, navigating CMMC requirements can be overwhelming, especially when confronted with its most challenging controls.

This webinar explores the ten most challenging CMMC requirements, such as CUI encryption, multifactor authentication, and incident response testing, unpacking why these standards can be difficult to meet.
Why are gaps so common in these critical areas? Technical complexity, unfamiliarity, and a lack of in-house expertise often play significant roles, particularly for small and mid-sized organizations. But challenges are not roadblocks; they are invitations for growth.
Practical Strategies Outlined
By understanding these requirements deeply, planning strategically, and leveraging resources effectively, companies can build a robust compliance strategy that protects both their data and their future. In the following webinar, we’ll dive into each requirement, examine the reasons behind frequent compliance gaps, and outline practical strategies to address and excel in meeting these CMMC standards.
Whether you’re just beginning your compliance journey or looking to refine your current practices, this webinar will provide the insights and guidance needed to navigate these demanding CMMC requirements with confidence and clarity.
Tackling the Tough Ten: Strategies for the Hardest CMMC Requirements
Description: This session breaks down the ten most challenging aspects of CMMC compliance. It offers practical strategies, expert tips, and resources to turn these hurdles into milestones on your compliance journey.
What are the Ten Most Challenging CMMC Requirements?
According to https://www.dcma.mil/DIBCAC/ the most difficult CMMC Requirements are:
-
- CUI Encryption
- Multifactor Authentication
- Flaw Remediation
- Risk Assessment
- Vulnerability Scan
- Event Review
- Audit Correlation
- Incident Response Testing
- System Baselining

Why are Gaps in these 10 CMMC Practices so Common?
The most challenging CMMC requirements—like CUI encryption, multifactor authentication, and incident response testing—are difficult to meet for several reasons, often creating significant compliance gaps within organizations. These requirements involve technical complexity, new controls, and specialized knowledge, making them difficult for many companies, especially small and mid-sized ones, to fully understand and implement.
Here’s why gaps in these critical areas are so prevalent:
Technically Complex
Many of the CMMC requirements, such as encryption and vulnerability scanning, involve advanced technical processes that demand a deep understanding of cybersecurity principles and specialized tools. For instance, encryption requires careful configuration, and any mistakes in implementing CUI or FIPS-validated encryption can lead to data exposure, despite efforts to keep information secure.

Similarly, vulnerability scanning and audit correlation require expertise in monitoring tools and interpreting results to identify and mitigate risks effectively. For companies without dedicated cybersecurity resources, navigating these complexities can be overwhelming.
Introduction of New Controls
CMMC standards often introduce new controls that many companies have not previously implemented, such as multifactor authentication (MFA) for accessing critical systems or event review mechanisms to monitor security incidents. The adoption of these controls requires time, resources, and adaptation to new security practices, which can feel like a burden, especially for smaller organizations. Adding new layers of security demands changes in user behavior and administrative policies, which can lead to resistance, delays, or incomplete implementation.
Lack of In-House Expertise
Meeting CMMC requirements is further complicated by the fact that many companies lack the specialized knowledge required to properly implement these controls. Requirements like system baselining and incident response testing involve niche skills in configuration management and cybersecurity operations that general IT staff may not possess. Without cybersecurity experts to guide the process, organizations may struggle to implement these requirements effectively. This expertise gap is particularly noticeable in smaller companies, where IT resources are often limited, and hiring specialized staff may be financially challenging.
Financial Constraints and Resource Limitations
Implementing and maintaining these controls often requires significant investment, not only in terms of direct costs for new technology and tools but also in ongoing staff training and process management. The continuous need for updates, scanning, monitoring, and testing (e.g., with incident response testing and flaw remediation) creates additional demands on budgets that are often constrained in smaller organizations. Limited resources can also mean that companies cannot dedicate staff solely to compliance, resulting in gaps due to multitasking or de-prioritization of certain requirements.
Operational Disruption
Some requirements, like multifactor authentication and encryption, may disrupt existing operations. Implementing MFA, for example, may require reconfiguring user access procedures, which can inconvenience employees and impact productivity. Incident response testing and audit correlation also require continuous vigilance, potentially impacting operational flow.

These disruptions can make full adoption challenging, especially in organizations where workflows are tightly controlled and time-sensitive.
Rapidly Evolving Cyber Threats
The cybersecurity landscape is constantly evolving, with new threats emerging that exploit any weaknesses in security measures. Requirements like vulnerability scanning, event review, and flaw remediation necessitate an ongoing commitment to identifying and responding to potential security issues. As the threat environment changes, maintaining compliance becomes a moving target, adding an additional layer of difficulty for companies trying to keep up with both CMMC standards and the latest security threats.
Insufficient Automation
Automation can help with tasks like system baselining, vulnerability scanning, and event review, but many companies either lack access to the necessary tools or aren’t leveraging them to their full extent. Manual processes introduce a higher risk of error, and without automated monitoring and alerts, organizations are likely to overlook key compliance requirements.
Challenges in Documentation and Reporting
CMMC compliance involves thorough documentation and reporting for each requirement, which can be an administrative burden. Many companies lack established processes for tracking compliance data, maintaining audit logs, and creating reports that will satisfy CMMC assessors. Without these processes, even organizations that meet technical requirements may struggle to demonstrate compliance during an audit.
These challenges combine to create common gaps in CMMC compliance, but they can be overcome with strategic planning, external support, and investment in the right tools and training. By addressing these underlying obstacles, organizations can not only close compliance gaps but also enhance their overall security posture.
What Strategies Can We Use to Navigate the Challenging Requirements of CMMC?
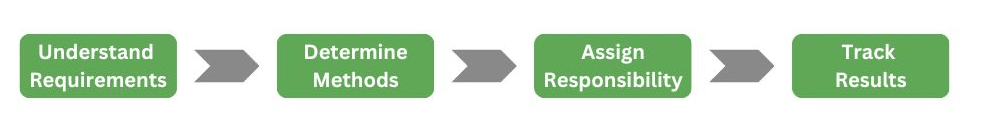
Gain a good understanding of each requirement.
Ask, “What’s really required?”, “How does it help improve security?” and “What will we have to show an assessor?”
Determine how to meet the requirement.
Ask, “What methods can we use to meet each requirement?”, “What options are available?” and “Which option is best for our situation?”
Assign responsibility.
“Who is taking responsibility to implement and maintain each requirement?” “What is the deadline for implementation?”
Track results.
“How will we monitor each requirement?” “How often should we verify each requirement?”
CUI Encryption
What Is the Purpose of Cryptology and Encryption?
-
- Encryption transforms data into unreadable formats to protect sensitive information like CUI from unauthorized access.
- FIPS-Validated Encryption: (lower third) Only encryption methods that meet U.S. government standards (FIPS) can be used to secure CUI, ensuring strong, tested protection.
- Encryption purpose: Even if data is intercepted, encryption ensures it remains secure unless the correct decryption key is used.
When Is Encryption Required?
-
- Data in transit
- Remote access
- Passwords
- Portable storage
- Wireless access
- Mobile devices
What Does FIPS-Validated Cryptography Mean?
FIPS-validated cryptography refers to encryption algorithms that have been tested and approved by the National Institute of Standards and Technology (NIST) under the Federal Information Processing Standards (FIPS) lower third (two separate lines). It ensures that the cryptography meets strict government security standards, particularly for protecting sensitive data like CUI.

CMMC requires FIPS 140-2 or FIPS 140-3 when protecting CUI (Controlled Unclassified Information)
What Are Some Common Methods for Deploying FIPS-Validated Encryption?
Use Built-In OS Tools:
Many operating systems (like Windows and Linux) offer FIPS-compliant encryption options that can be enabled in security settings.
Deploy FIPS-Certified Software:
Choose software solutions (e.g., VPNs, storage encryption) that specifically advertise FIPS-validated cryptography.
Leverage Cloud Services:
Many cloud providers offer FIPS-validated encryption as part of their security services, simplifying deployment.
Multifactor Authentication
What is the Purpose of MFA?
Enhanced Security:
MFA reduces the risk of unauthorized access by requiring two or more forms of verification (for example, password + phone app).
Protection of Sensitive Data:
It helps protect critical systems and CUI by making it harder for attackers to breach accounts.
Mitigates Credential Theft:
Even if passwords are stolen, MFA prevents immediate access without the second factor.
When is MFA Required to be in Use?
Several CMMC practices indicate that MFA is required to be in use:
-
- For local and network access to privileged accounts and for network access to non-privileged accounts.
- To establish nonlocal maintenance sessions via external network connections and terminate such connections when nonlocal maintenance is complete.
Note: You might want to start with privileged accounts and expand MFA to all users over time.
Handling Vulnerabilities and Risks
Vulnerability Scanning
What is the Purpose of Vulnerability Scanning?
Proactive Risk Management:
Scanning identifies vulnerabilities that need fixing to reduce the risk of cyberattacks.
Continuous Monitoring:
Regular scans ensure that new vulnerabilities, such as those introduced by software updates or configuration changes, are detected quickly.
When is it Necessary to Implement Vulnerability Scans?
-
- Periodically – for vulnerabilities in organizational systems and applications
- When new vulnerabilities affecting those systems and applications are identified.
What Affordable or Free Tools are Available for Small Businesses to Conduct Vulnerability Scans?
OpenVAS:
A free, open-source vulnerability scanner that provides detailed scanning and reporting capabilities.
Qualys Community Edition:
Offers limited free scanning services for small businesses, helping identify vulnerabilities in web apps and networks.
Nmap:
A free network discovery tool that can also be used for basic vulnerability scanning and security auditing.
Small businesses often overlook the importance of vulnerability scanning after new updates. This is critical to maintain security.
Risk Assessment
What is the Purpose of Risk Assessments?
Identify Threats:
It helps pinpoint potential vulnerabilities and threats to systems and data.
Prioritize Security Risks:
Allows organizations to focus resources on mitigating the most significant risks.
Continuous Improvement:
Provides a roadmap for improving security posture over time and adapting to new threats.
When are Risk Assessments Required?
Risk assessments should be ongoing. Every time there’s a significant change in the system or environment, reassess the risks.
It’s best to assign a dedicated person, even if it’s a shared role, to ensure that risk assessments don’t fall by the wayside.
There’s a lot to consider when it comes to vulnerability scanning and risk assessments. If you don’t perform regular scans and assess your risks thoroughly, you’re leaving your organization open to potential threats and weaknesses. These processes are essential not just for compliance, but for ensuring your systems remain secure against evolving risks.

Audit Correlation
Incident Response and Audit Logging
Incident response and audit logging are often overlooked until something goes wrong. How can a small business proactively address these areas? How can a business manage audit logs and incident response?
What are Audit Logs in Networking?
Tracking User Activity:
Logs record who accessed the network, when, and what actions were taken.
Security Monitoring:
They provide visibility into potential security incidents or policy violations.
When it comes to Audit Logging, what are the Key Events that Should be Logged and Reviewed Regularly?
-
- Focus on logging access to critical systems and any changes to configurations. These logs are vital during an investigation.
- Set up automated alerts for key events to ensure nothing is missed.
Audit logs capture details
-
- about system configuration changes and access events,
- with details to identify who was responsible for the activity,
- when and where the activity took place, and
- what the outcome of the activity was.
Automated log analysis supports near real-time detection of suspicious behavior.
What Kinds of Tools are Available to Help with Audit Logging?
SIEM (System Information and Event Management)
Incident response and audit logging are critical to maintaining security and compliance. If your business doesn’t have a tested plan for handling incidents, you’re vulnerable to extended downtime and potential data loss.
Likewise, without proper audit logs, you won’t have the visibility needed to detect and respond to suspicious activity. Make sure your plans are clear, well-practiced, and supported by the right tools to protect your organization.
Incident Response
What are the Essentials of a Good Incident Response Plan for a Small Business?
-
- Start with clear roles and responsibilities. Everyone should know who to call and what to do.
- Clearly outline easy-to-follow steps for detection, containment, analysis, and recovery.
- Develop an incident response policy.
Incident Response Testing
How Should a Business Test its Incident Response Plan, and How Often?
Regularly test your incident response plan, even if it’s through a simple tabletop exercise.
Configurations
The importance of maintaining baseline configurations and inventories.
System Baselining
What is a Baseline Configuration?
A baseline configuration is a defined and approved set of system settings, software, and hardware that serve as a secure starting point for all devices and systems in an organization.
Consistency:
Ensures all systems are set up the same way, reducing configuration drift.
Security:
Establishes a secure configuration that minimizes vulnerabilities.
Change Management:
-
- Helps track and control changes to systems, ensuring they remain aligned with security standards.
- Make sure that any new hardware or software goes through a review process before being added to the environment.
What are the Biggest Challenges in Maintaining Baseline Configurations, and How Can Small Businesses Overcome Them?
Configuration Drift:
Systems gradually change over time due to updates or manual changes.
Solution:
Use automated tools to regularly audit and enforce baseline configurations.
Limited Resources:
Small businesses often lack dedicated IT staff.
Solution:
Outsource to managed service providers (MSPs) or use affordable configuration management tools.
Keeping Up with Changes:
As software and hardware evolve, updating baselines becomes complex.
Solution:
Establish a regular review process to update baselines as new technologies are implemented.
How Should a Small Business Keep Track of Hardware and Software Inventories Effectively?
-
- Documenting changes is critical. Even a simple spreadsheet can work as a starting point.
- Use tools that automate inventory tracking and configuration management to reduce manual effort.
- Keep an inventory not just of what you have, but also of what you’ve decommissioned.
Maintaining baseline configurations is essential for consistency, security, and compliance, but it can be a challenge for small businesses.
Without proper controls, configuration drift and outdated baselines can expose your organization to vulnerabilities.
By automating audits, documenting changes, and regularly reviewing your configurations, you can maintain a secure and manageable environment with minimal effort.
CMMC Compliance Approaches for Small Businesses with Limited IT Support
How can a company with limited resources prioritize its efforts effectively?
-
- Start with a gap analysis to understand where you stand against the requirements.
- Prioritize essential CMMC requirements like multifactor authentication, encryption, and incident response, which can significantly reduce risk.
- Use low-cost tools or services to automate tasks like vulnerability scanning and baseline configuration management.
How Does Scope Affect Implementation of The CMMC Requirements?
-
- Limit the assessment to only those systems handling CUI, which reduces the number of systems and requirements that need to be addressed.
- Prioritize implementing controls on high-risk systems where CUI is processed or stored.
- A more focused scope means fewer resources are needed for implementation, allowing small businesses to concentrate efforts on securing critical areas first.
It’s clear that these and other CMMC requirements are highly technical and require special expertise. What can a small business do if that is the case?
For small businesses without dedicated IT resources, partnering with external experts can be the most effective solution.
Outsource to Managed Service Providers (MSPs):
MSPs can provide the expertise needed to manage and implement CMMC requirements without the cost of hiring full-time staff.
Leverage Cybersecurity Consultants:
Engage with cybersecurity consultants who specialize in CMMC to guide you through the process and ensure compliance.
Utilize Government and Industry Resources:
There are a number of free or low-cost resources, such as guides, templates, and training programs, offered by government agencies like NIST or through industry associations.”
Leverage Cloud Providers:
Many cloud providers, like Core, have built-in security features that meet CMMC requirements, reducing the need for in-house technical expertise. We offer a cloud-based system called CORE Vault built for small businesses who need an alternative to upgrading their network with controls like we’ve discussed today.
Consider Cybersecurity as a Service (CaaS):
Some vendors offer CaaS, where they manage your security operations and ensure compliance with CMMC for a fraction of the cost of hiring IT personnel.
We have focused today on the Toughest requirements of CMMC and I hope you have a better understanding of the technical requirements you’ll have to meet if you pursue CMMC certification next year.
If you would like to speak to someone about your own situation or would like information about our CORE Vault cloud-based solution, members of our consulting team are available to assist you.
About CORE Vault for NIST CMMC
Everything you need for NIST/CMMC in one cloud-based solution. The CORE Vault CUI Enclave and Consulting Services.
If you contract with the Department of Defense, you require advanced cybersecurity protections. To comply with DFARS, you need to meet the requirements of NIST SP 800-171. Soon, DoD contractors will also need to meet the requirements of Cybersecurity Maturity Model Certification (CMMC 2.0). However most contractors don’t have the resources to overhaul their entire network for compliance. With CORE Vault, you don’t have to.
With CORE Vault, you can separate government data from your network and access it through a secure, cloud-based environment managed by our cyber experts.
CORE Vault also includes the support needed to reach full compliance with the non-technical cybersecurity requirements, such as your system security plan and required policies.
We’ve seen contractors achieve their maximum DoD-required SPRS score in 30 days.

Core Business Solutions, established in 2000, is a Registered Practitioner Organization through the Cyber AB and has been providing consulting and technical solutions for NIST/CMMC for over 5 years. Rick Krick is the Director of Security Solutions for Core Business Solutions and directs our Cybersecurity Services solutions including CMMC. Rick has over 25 years of experience in Management System implementations, software development, IT services, and certifications.

