CMMC 2.0 Compliance Explained
An Integrated, Layered Approach to Cybersecurity
Amid rising cyber threats, the Department of Defense (DoD) has developed a robust framework to ensure its contractors safeguard sensitive information. The Cybersecurity Maturity Model Certification (CMMC) 2.0 serves as a critical element in this defense, building on previous cybersecurity requirements such as DFARS 252.204-7012 and NIST SP 800-171.
Designed to enforce stringent cybersecurity standards across the defense industrial base (DIB), CMMC 2.0 introduces a streamlined approach that focuses on protecting Controlled Unclassified Information (CUI) and enhancing accountability. This comprehensive guide examines the CMMC 2.0 compliance process, providing defense contractors with the essential knowledge to navigate this evolving cybersecurity landscape.

Background for CMMC Compliance:
The Cybersecurity Maturity Model Certification (CMMC) was developed by the Department of Defense (DoD) to ensure that defense contractors meet specific cybersecurity standards, protecting sensitive unclassified information like Controlled Unclassified Information (CUI) from increasingly sophisticated cyberattacks.
The introduction of CMMC builds on prior frameworks and requirements, including DFARS 252.204-7012 and NIST SP 800-171, adding layers of oversight, accountability, and certification to the defense industrial base (DIB).
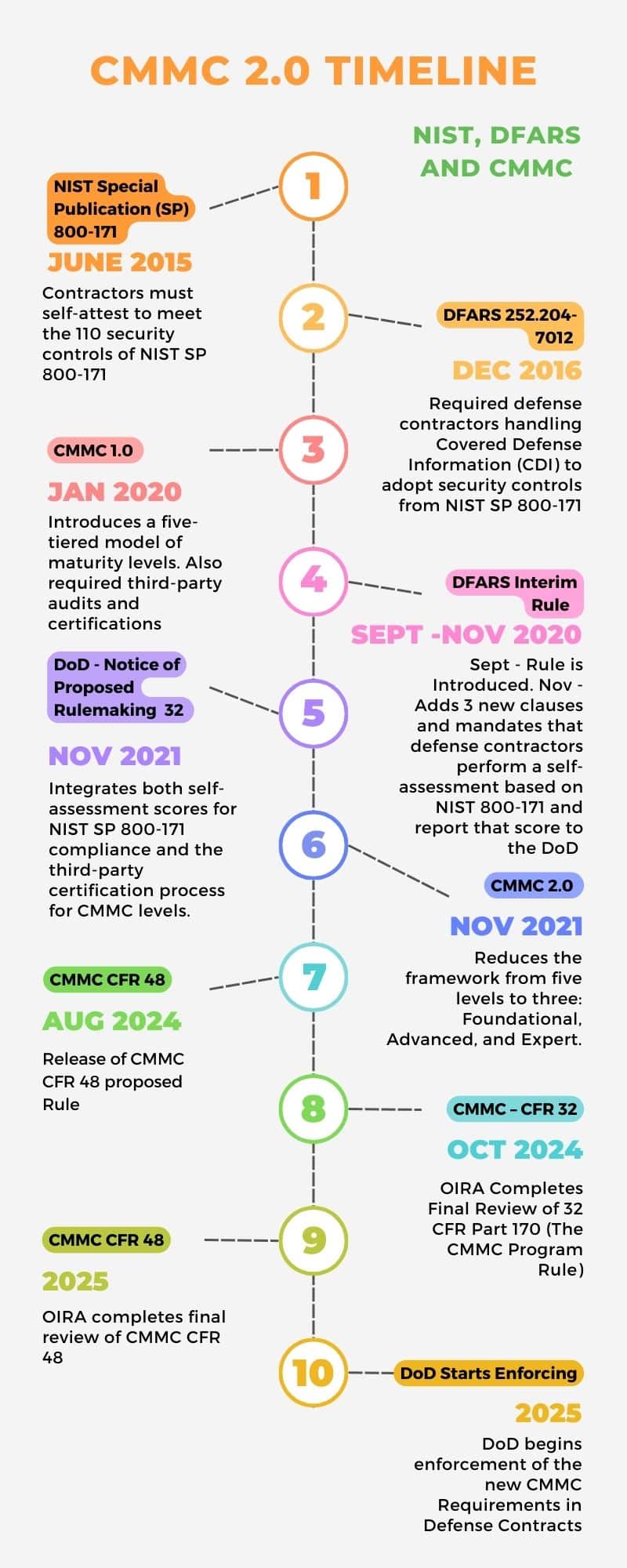
Timeline of Events for CMMC Compliance:
1. NIST Special Publication (SP) 800-171 (2015):
Published in June 2015, NIST SP 800-171 provides a set of 110 security controls that organizations must implement to protect the confidentiality of CUI (Controlled Unclassified Information) in non-federal systems.
These controls cover access control, incident response, media protection, system monitoring, and more.
Applicability: The standard is required for defense contractors and other organizations that handle sensitive government information but are not part of the federal government.
Objective: To create a consistent framework for securing sensitive unclassified information within the private sector.
2. DFARS 252.204-7012 (2016):
Defense Federal Acquisition Regulation Supplement (DFARS) 252.204-7012 was implemented in December 2016 and requires defense contractors handling Covered Defense Information (CDI) to adopt security controls from NIST SP 800-171.
This clause mandates contractors to implement appropriate safeguards to protect CDI (Covered Defense Information), ensuring compliance with the security standards outlined in NIST SP 800-171.
It also requires contractors to report cyber incidents to the DoD within 72 hours of discovery and retain evidence for possible forensic analysis.
Objective: Strengthen the security of sensitive information within the DIB.
3. CMMC 1.0 (January 2020):
In response to persistent cyber threats and the need for better enforcement of cybersecurity standards across the defense industrial base, the DoD introduced the Cybersecurity Maturity Model Certification (CMMC) framework in January 2020.
CMMC 1.0 introduced a five-tiered model (CMMC Level 1 to Level 5) to assess the maturity of contractors’ cybersecurity practices.
Each level had increasingly stringent requirements based on the type of data the contractor managed, with Level 5 reserved for the highest security needs.
Unlike DFARS 252.204-7012 and NIST SP 800-171, CMMC required third-party audits and certifications, meaning contractors needed independent verification of their compliance.
Objective: To enhance security across the defense supply chain through a certification model.
4. DFARS Interim Rule (Sept – Nov 2020)
The DFARS Interim Rule, issued in September 2020, introduced new cybersecurity requirements for Department of Defense (DoD) contractors. Specifically, it mandated compliance with the National Institute of Standards and Technology (NIST) Special Publication 800-171 for protecting Controlled Unclassified Information (CUI). The rule established three key elements:

Self-Assessment Reporting:
Contractors must conduct a self-assessment of their cybersecurity posture against the 110 controls outlined in NIST SP 800-171. The results must be entered into the DoD’s Supplier Performance Risk System (SPRS).
CMMC Implementation:
The rule paved the way for the phased implementation of the Cybersecurity Maturity Model Certification (CMMC), requiring contractors to eventually be certified at different levels depending on the sensitivity of the data they handle. This would ensure a third-party verification of their cybersecurity capabilities.
Incident Reporting and Security:
The rule reinforced the need for timely reporting of cyber incidents. It emphasized protection against threats such as malicious software, media protection, and forensic analysis access, all required under DFARS clause 252.204-7012.
This interim rule was part of the broader push by the DoD to secure its supply chain from cyber threats and was followed by updates and further rulemaking to finalize the requirements.
What are the Three Interim Rule Clauses?
DFARS Clause 252.204-7019, 7020, and 7021:
DFARS 252.204-7019:
Requires contractors to submit a self-assessment of their compliance with NIST SP 800-171 controls, using a Supplier Performance Risk System (SPRS) score. This interim rule ensures contractors are required to meet baseline cybersecurity standards before achieving CMMC certification.
DFARS 252.204-7020:
Establishes the requirement for contractors to provide the DoD with access to their facilities, systems, and personnel to assess compliance with NIST SP 800-171.
DFARS 252.204-7021:
This is the clause that formalizes the requirement for CMMC certification. Contractors are required to achieve the appropriate CMMC level (depending on the sensitivity of the information being handled) before being awarded a contract.
Consulting Support for CMMC Compliance
At Core, we offer a modular approach to certification. We break the requirements down into two broad categories: organizational and technical. We provide NIST/CMMC training for your employees, your management, and your IT Team or MSP (if you outsource your IT needs).
We also help you with your guided self-assessment.
We will help you develop your System Security Plan (SSP), Plan of Action and Milestones (POAM), Roadmap, and budget. Core Business Solutions is a NIST/CMMC registered practitioner organization (RPO). Click to view CBS CMMC Consulting Offering Sheet Link.

5. Notice of Proposed Rule Making 32 (November 2021)
The CMMC DFARS Proposed Rule 32 focuses on incorporating the Cybersecurity Maturity Model Certification (CMMC) framework into the Defense Federal Acquisition Regulation Supplement (DFARS), particularly under Title 32 of the Code of Federal Regulations (CFR).
This rule is designed to strengthen the cybersecurity requirements for contractors working with the Department of Defense, ensuring they comply with specific standards based on the sensitivity of the data they manage.

6. CMMC 2.0 (November 2021):
In response to industry feedback and to streamline the CMMC program, the DoD released CMMC 2.0 in November 2021, significantly simplifying the original CMMC model.
Key Changes:
Reduced the framework from five levels to three:
Level 1 (Foundational): Equivalent to basic cybersecurity practices already in place for all defense contractors, primarily self-assessed.
Level 2 (Advanced): Based on NIST SP 800-171 standards, required for handling CUI, with a mix of self-assessments and third-party certifications.
Level 3 (Expert): For handling more critical data, involving higher security standards, with continuous third-party assessments.
Certification: CMMC 2.0 allows for some self-assessment for lower-tier contractors (Level 1), but higher levels require third-party audits.
Objective: To simplify implementation while maintaining strong cybersecurity standards across the defense supply chain.
7. OIRA Completes Final Review of CMMC CFR 32 (October 2024)
What is the 32 CFR Part 170 About and How Does it Relate to CMMC?
In the context of CMMC (Cybersecurity Maturity Model Certification), Rule 32 refers to the Defense Federal Acquisition Regulation Supplement (DFARS) Rule 32. This rule specifically relates to the DFARS interim rule that was introduced in September 2020. It includes the establishment of requirements for contractors to meet CMMC compliance and outlines how the DoD will verify that contractors are adhering to cybersecurity requirements.
Key Points of DFARS Rule 32 Regarding CMMC:
Introduction of CMMC Requirements:
DFARS Rule 32 integrates CMMC requirements into the DoD’s contracting process. Contractors who work with the Department of Defense (DoD) are required to comply with CMMC standards as part of the contract award process.
It also introduces the concept of CMMC certification as a prerequisite for bidding on or continuing to hold DoD contracts.

Implementation Timeline:
32 CFR Part 170 (The CMMC Program Rule) allows the gradual rollout of CMMC requirements across contracts. It states that by 2026, all DoD contracts will require compliance with CMMC standards at the appropriate level.
This rule was finalized and published in October of 2024. It officially establishes the Cybersecurity Maturity Model Certification (CMMC) Program. The rule is effective 60 days after publication in the Federal Register, which means the program will take effect by December 2024.
In the meantime, contractors must continue to meet NIST SP 800-171 requirements and submit their self-assessment scores as part of the bidding process, with some contracts requiring a formal CMMC certification.
Oversight and Enforcement:
The CMMC Program Rule empowers the DoD to assess contractors’ cybersecurity practices more rigorously. It integrates both self-assessment scores for NIST SP 800-171 compliance and the third-party certification process for CMMC levels.
This rule is intended to improve oversight and ensure that contractors handling Controlled Unclassified Information (CUI) or other sensitive data meet the required security standards.
DFARS Rule 32, with CMMC, formalizes the process through which the DoD will enforce CMMC requirements within the defense industrial base.
It mandates cybersecurity compliance, self-assessment, and third-party certification to ensure contractors are protecting sensitive information in line with the evolving CMMC standards. Rule 32 establishes the framework for how CMMC is implemented and integrated into defense contracts.
8. Release of CMMC CFR 48 Proposed Rule (August 2024)
How will the New Proposed Rule (48) affect CMMC 2.0 Requirements?
The new proposed Rule 48 will significantly impact CMMC 2.0 requirements by integrating the CMMC framework into the Defense Federal Acquisition Regulation Supplement (DFARS), which governs DoD contracts.
Here are the central ways this rule will affect CMMC 2.0:
1. Mandatory CMMC Certification
Contractors, including both prime and subcontractors, must secure the appropriate CMMC certification level before being awarded a contract and are obligated to maintain that certification throughout the contract’s duration. This ensures that every entity within the supply chain complies with strict cybersecurity protocols, safeguarding sensitive information across all levels of engagement.
2. New Compliance and Reporting Requirements:
Annual Compliance Declarations:
Contractors will be required to annually confirm their adherence to CMMC standards, particularly when there are any changes to their security posture. This declaration must come from a senior executive, reinforcing top-level accountability and emphasizing the organization’s commitment to maintaining robust cybersecurity practices.
72-Hour Notification Requirement:
Contractors must report any breaches in CMMC compliance or security issues to the contracting officer within 72 hours. This decentralized reporting structure demands heightened awareness and rapid response to ensure timely communication of potential risks.
3. Risk of Certification Loss:
The rule includes a clause stating that modifications to a contractor’s information systems could potentially void their CMMC certification. Contractors must ensure that any system changes remain in alignment with CMMC requirements to avoid jeopardizing their certification status.
4. Phased Rollout:
The proposed rule outlines a step-by-step introduction of CMMC 2.0 requirements across defense contracts, allowing contractors a transition period to achieve full compliance. However, early preparation is crucial, as these requirements are set to be fully enforced across all applicable contracts by 2025.
Rule 48 formalizes the integration of CMMC 2.0 into DoD contracting, with stricter oversight, continuous compliance requirements, and potential penalties for lapses. Contractors must prepare early to ensure they meet these new cybersecurity demands.
9. OIRA completes final review of CMMC CFR 48 (2025)
10. DoD begins enforcement of the new CMMC Requirements in Defense Contracts (2025)
What is the Relationship Between CMMC, DFARS, and NIST?
CMMC (Cybersecurity Maturity Model Certification) and DFARS (Defense Federal Acquisition Regulation Supplement) 252.204-7012 are both part of the U.S. Department of Defense’s (DoD) broader initiative to protect sensitive unclassified information within the defense industrial base.
NIST (National Institute of Standards and Technology) SP 800-171 is part of the Department of Commerce. Although they all serve the same overarching goal, they have distinct roles and responsibilities that complement each other in terms of cybersecurity compliance.

NIST SP 800-171
NIST SP 800-171 Framework: Both CMMC and DFARS 252.204-7012 are based on the security controls outlined in NIST SP 800-171, which defines the practices needed to safeguard CUI in non-federal systems. CMMC, however, formalizes the enforcement of these controls through certification.
DFARS 252.204-7012:
Purpose: DFARS 252.204-7012, which was implemented in 2016, requires defense contractors and subcontractors to implement specific cybersecurity measures outlined in NIST SP 800-171 to protect Covered Defense Information (CDI) and Controlled Unclassified Information (CUI).
Compliance: Contractors must self-attest to meet the 110 security controls of NIST SP 800-171. Additionally, they are required to report any cyber incidents to the DoD within 72 hours and maintain evidence for potential forensic analysis.
Scope: This clause applies to contractors that handle CDI or CUI and mandates compliance with NIST SP 800-171 but does not initially require external certification or third-party audits to verify compliance.
CMMC:
Purpose: CMMC was introduced to add a certification and verification layer to the existing DFARS cybersecurity requirements. It was created to address weaknesses in self-attestation and ensure that defense contractors were properly implementing and maintaining cybersecurity practices.
Compliance: Unlike DFARS 252.204-7012, which allowed self-attestation, CMMC requires contractors to be certified based on their level of cybersecurity maturity. Depending on the CMMC level, certification may be achieved through self-assessment or third-party audits.

Scope: CMMC builds on DFARS and NIST SP 800-171 by introducing a tiered model with varying levels of security requirements based on the sensitivity of the information contractors manage. The model evolved from CMMC 1.0’s five levels to CMMC 2.0’s simplified three levels, with certification being mandatory for specific contracts.
How do CMMC, DFARS, and NIST Work Together?
DFARS sets the baseline:
DFARS 252.204-7012 lays the foundation by requiring defense contractors to implement NIST SP 800-171 controls to protect CUI and CDI.
CMMC builds on DFARS:
CMMC takes this foundation a step further by requiring contractors to undergo a formal certification process, ensuring these controls are correctly implemented and maintained.
Enforcement through CMMC:
The introduction of CMMC addresses a key issue with DFARS—many contractors were not fully compliant with NIST SP 800-171 despite self-attesting. CMMC brings a higher level of accountability and forces contractors to meet cybersecurity requirements through independent audits.
CMMC and DFARS are complementary parts of the DoD’s strategy to safeguard sensitive information within the defense industrial base.
DFARS provides the regulatory requirement to implement cybersecurity measures, while CMMC enforces these requirements through mandatory certification and external oversight, ensuring that defense contractors not only implement but also maintain strong cybersecurity practices.
Summary
This article outlines the U.S. Department of Defense’s (DoD) efforts to secure sensitive information within its defense industrial base through the Cybersecurity Maturity Model Certification (CMMC) 2.0. Building on previous frameworks like DFARS 252.204-7012 and NIST SP 800-171, CMMC 2.0 aims to enhance cybersecurity by introducing a streamlined, three-tiered model of certification that mandates different levels of compliance based on the sensitivity of the data handled.
This article also explores the integration of cybersecurity requirements into defense contracts, and how contractors must meet various certification levels, from self-assessments for basic security to third-party audits for advanced practices. Ultimately, CMMC 2.0 aims to enhance the security of Controlled Unclassified Information (CUI) while fostering greater accountability and safeguarding the defense supply chain against growing cyber threats.
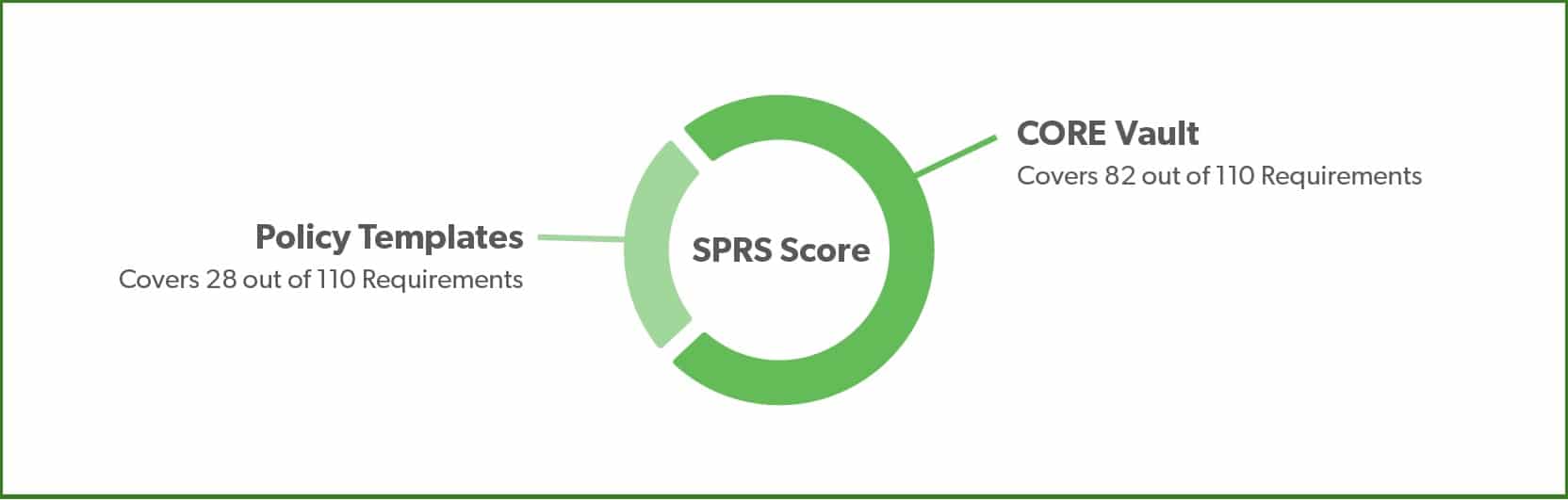
About CORE Vault for NIST CMMC
Everything you need for NIST/CMMC in one cloud-based solution. The CORE Vault CUI Enclave and Consulting Services.
If you contract with the Department of Defense, you require advanced cybersecurity protections. To comply with DFARS, you need to meet the requirements of NIST SP 800-171. Soon, DoD contractors will also need to meet the requirements of Cybersecurity Maturity Model Certification (CMMC 2.0). However most contractors don’t have the resources to overhaul their entire network for compliance. With CORE Vault, you don’t have to.
With CORE Vault, you can separate government data from your network and access it through a secure, cloud-based environment managed by our cyber experts.
CORE Vault also includes the support needed to reach full compliance with the non-technical cybersecurity requirements, such as your system security plan and required policies.
We’ve seen contractors achieve their maximum DoD-required SPRS score in 30 days.
Core Business Solutions, established in 2000, is a Registered Practitioner Organization through the Cyber AB and has been providing consulting and technical solutions for NIST/CMMC for over 5 years. Rick Krick is the Director of Security Solutions for Core Business Solutions and directs our Cybersecurity Services solutions including CMMC. Rick has over 25 years of experience in Management System implementations, software development, IT services, and certifications.




