Essential Policies and Procedures for Cyber Defense
Blueprint for Security: Essential Policies and Procedures for Cyber Defense
On October 15, 2024, the Department of Defense (DoD) unveiled the finalized Cybersecurity Maturity Model Certification (CMMC) rule in the Federal Register, signaling a transformative move towards fortified cybersecurity compliance within the defense industrial base (DIB).
This final rule introduces a phased implementation of CMMC requirements, calling contractors, subcontractors, and small businesses alike to proactively ready themselves for its integration into defense contracts in the coming years.
Everyone from large prime contractors to subcontractors and suppliers who supply products and services to support DoD contracts will be impacted by this new contractual requirement. This webinar will help you with preparations for achieving CMMC compliance and certification.

Cybersecurity Experts Discuss CMMC Policies and Procedures
Cybersecurity experts Scott Dawson, President of Core Business Solutions, and Rick Krick, Director of Security Solutions, explain what is required and provide several practical suggestions for making your documentation as efficient and effective as possible.
Becoming CMMC Level 2 Certified
To become CMMC Level 2 certified, you have to demonstrate that you have implemented 110 security requirements found in NIST SP 800-171 and CMMC 2.0. Those requirements are grouped into 14 topic areas called “families” or “domains”. During an assessment, your assessor will drill into 320 specific assessment objectives to verify your cybersecurity practices meet the requirements.
That means that there is a lot of detail that needs to be well understood, effectively implemented, and able to be demonstrated to the assessor.
The starting point is the development of your documentation, which includes policies and procedures for cybersecurity.
Now we turn our attention to more tactical areas starting with documentation. While you work on your documentation you can also be working on implementing your security practices. By working in unison, you can be sure to implement what is required, but only what is required.
Blueprint for Security- Essential Policies & Procedures for Cyber Defense
Description: Establish a solid cybersecurity foundation with the right policies and procedures. This webinar guides you through the essential documents your business needs, from incident response plans to data protection policies.
Documentation and Implementing CMMC Compliance
What are the 3 Primary Reasons to have Documentation for your Cybersecurity Program?
It helps you learn the requirements.
Helps management determine how the company will meet NIST and CMMC requirements. As they read specific requirements in the standards, they then will ask “how”, “who”, “when”, and “what” type questions to spell out their company security controls.
It helps you communicate the requirements.
Build a culture of security within the organization. Communicates the company’s rules and guidelines for security practices. Helps employees learn their roles and responsibilities and specifically what is expected. It gives them an “authoritative source” for information.
It helps you demonstrate compliance with the requirements.
Demonstrate compliance with NIST and CMMC requirements.
Documentation is required and will be a large area of focus during an assessment. Documentation serves as evidence of security controls that have been implemented.
Documentation can also make an audit or assessment go more smoothly since it explains how the company meets the requirements in clear, concise language. Of course, this assumes that the documentation is accurate and regularly updated as requirements or company practices change. Otherwise, documentation can signal that a requirement is not being correctly met.
What Documentation is Required for CMMC?
Documentation falls into 2 categories:
1. Those types of documents used to define and manage your cybersecurity program and
2. Those that are used as evidence and artifacts (records) to demonstrate the performance of your program and compliance with NIST and CMMC requirements.
What are Some Examples of Documentation Required for your Cybersecurity Program?
-
- System Security Plan (SSP)
- Plan of Action and Milestones (POAM)
- Network Diagram
- Data Flow Diagram
- Hardware and Software Inventory
- Responsibility Matrix
- Policies
- Procedures
We’ve talked about some of these in previous webinars, but these specific documents are required by every company seeking certification. They’re explicitly called out in the NIST and CMMC documents and they cover your entire scope of certification.
What Documentation can be used as Evidence and Artifacts?
Records and Logs
-
- Audit Logs and Records
- Configuration Settings and Associated Documentation
- Incident Response Records and Documentation
- Media Transport Records
- System Audit Logs and Records
- System Backup Logs or Records
Training Materials and Records
-
- Security Awareness Training Materials
- Training Records
Assessment Specific Documents
-
- List of System Accounts
- List of Privileged Functions and Associated User Account Assignments
- List of Identifiers Generated from Physical Access Control Devices
- Reports of Audit Findings
- Vulnerability Scanning Results
What do you mean by saying that Documents Can Be Used as Evidence and Artifacts?
Every documented policy, procedure, and implemented control serves as the basis of your compliance standing. Evidence not only reassures assessors of your commitment to cybersecurity but also serves as a tangible demonstration of the effectiveness of your security practices.

The NIST SP 800-171A, a companion document to CMMC requirements, details the structured approach for proving compliance, outlining three core assessment methods to ensure each requirement is met:
Examine, Interview, and Test.
Specifically, the “Examine” assessment method provides a framework for assessors to review various documents, records, and other artifacts that signify compliance.
This could include policies, incident response logs, access control lists, configuration settings, and audit reports, among others.
While not every item on the list is mandatory, selecting the right combination of artifacts is essential to provide assessors with an accurate, comprehensive view of your cybersecurity practices.
Documented Artifacts
Documented artifacts function as both a safeguard and a guidepost in CMMC assessments. They showcase your readiness, reveal gaps or weaknesses, and ultimately demonstrate that each control is implemented effectively.
In preparation, consider which documents and records will best support your compliance efforts, ensuring that they accurately reflect your organization’s security maturity.
In this way, evidence moves beyond mere paperwork; it becomes a powerful testament to the integrity and resilience of your organization’s cybersecurity framework.
The Proof is in the Pudding
“Proof is in the pudding”. During a CMMC assessment, “proof is in the evidence”.
In the companion document called NIST SP 800-171A, we learn that there are 3 methods used during an assessment to confirm that a requirement is met.
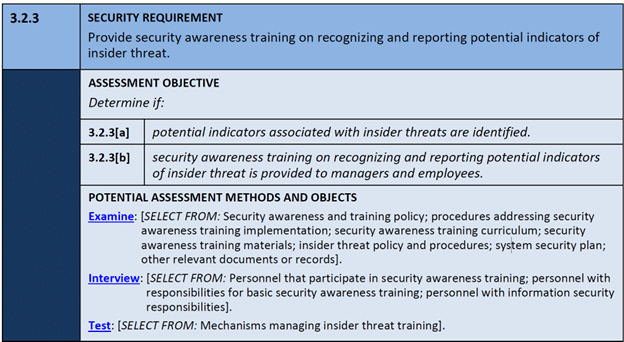
What is the “Examine” Assessment Method?
The “Examine” assessment method lists several examples of documentation and information that the assessor can review to evaluate compliance.
These are not all required, but you need to consider which of these may be needed to provide evidence that you have the requirement effectively implemented.
When it Comes to Cybersecurity, Why Are Policies Important?
In the realm of cybersecurity, well-defined policies are essential to build a secure, resilient, and compliant organization. Policies are more than just formal documents; they represent the high-level principles and rules that outline an organization’s approach to meeting security requirements.
They serve as a guiding framework for all decisions and actions across the company, including those of employees, contractors, and other stakeholders. Policies clarify what needs to be done, why it matters, and how it impacts the organization’s security, ensuring everyone is aligned with the company’s mission of protecting critical information.

Written Policies Provide a Shared Understanding
Without formalized policies, organizations would depend solely on verbal instructions and individual memory, which is both inconsistent and unsustainable. Different people may interpret expectations in varied ways, leading to discrepancies in actions and weakening the organization’s security posture.
Written policies provide a shared understanding of security standards and procedures, creating a foundation for consistency, efficiency, and accountability across departments. Everyone, from executives to entry-level staff, can rely on these documents to know exactly what’s expected, fostering a more cohesive and secure environment.
Policies Must be Customized to Address Unique Needs
Cybersecurity policies, in particular, are vital for protecting sensitive data and ensuring compliance with industry regulations. However, a one-size-fits-all approach won’t cut it. For policies to be truly effective, they must be tailored to address the unique needs and risks of the organization.
Simply using generic templates with a company logo slapped on won’t address the specific challenges that your business may face. By developing customized policies, companies can respond directly to their security landscape and regulatory demands, ensuring that the policies are not only relevant but also actionable and impactful in safeguarding the organization’s information assets.
What Policies are Required by NIST and CMMC?
-
- CMMC Domains
- Access Control (AC)
- Awareness & Training (AT)
- Audit & Accountability (AU)
- Configuration Management (CM)
- Identification & Authentication (IA)
- Incident Response (IR)
- Maintenance (MA) Media Protection (MP)
- Personnel Security (PS)
- Physical Protection (PE)
- Risk Assessment (RA)
- Security Assessment (CA)
- System and Communications Protection (SC)
- System and Information Integrity (SI)

Note: As you plan out your own policies you need to address all 14 domains.
What are some Examples of Typical Cybersecurity Policies?
Information Security Policy:
-
- Sets the overall approach to managing and protecting information assets.
- Defines the roles and responsibilities for information security within the organization.
- Outlines the key principles of information security, such as confidentiality, integrity, and availability.
Acceptable Use Policy:
-
- Specifies acceptable and unacceptable behaviors for using the organization’s IT resources.
- Covers topics such as internet usage, email communications, and the use of personal devices.
- Helps prevent misuse of IT resources and ensures that employees understand their responsibilities.
Access Control Policy:
-
- Defines how access to information and systems is granted, managed, and revoked.
- Establishes procedures for verifying user identities and assigning appropriate access levels.
- Ensures that only authorized individuals have access to sensitive information.
Incident Response Policy:
-
- Outlines the procedures for detecting, reporting, and responding to security incidents.
- Defines roles and responsibilities for the incident response team.
- Provides guidelines for communicating with stakeholders during and after an incident.
What Needs to be Included in a CMMC Written Policy?
Creating effective policies and procedures under the Cybersecurity Maturity Model Certification (CMMC) framework is critical for achieving compliance and establishing a solid cybersecurity posture. A well-crafted policy in the CMMC context is more than just a statement of intent—it needs to be actionable, specific, and aligned with the requirements of the certification level you’re aiming for.

Here’s what to include to ensure the policy serves both regulatory and operational needs:
1. Purpose and Scope
Purpose: Clearly outline why the policy exists. For example, its purpose might be to protect sensitive information, manage risks, or ensure compliance with federal regulations.
Scope: Define what and who the policy applies to, such as specific departments, employee roles, and applicable data or systems. Specify any exclusions where the policy might not apply.
2. Responsibilities and Roles
Identify the key individuals or teams responsible for implementing, maintaining, and enforcing the policy. This might include roles such as IT personnel, management, and designated cybersecurity officers.
Outline responsibilities so there’s clarity on accountability, especially if a breach or non-compliance issue arises.
3. Definitions and Terms
Define any technical jargon or acronyms (like FCI for Federal Contract Information or CUI for Controlled Unclassified Information) to ensure consistency and understanding across the organization.
4. Policy Statements
This is the core of your policy, where you state what must be done, prohibited, or restricted. Each policy statement should reflect CMMC requirements and include measurable actions or behaviors.
For instance, if the policy pertains to access control, specify requirements for user authentication, password complexity, and device restrictions.
5. Procedures for Compliance
Detail the specific steps or processes that individuals must follow to comply with the policy. This section should be prescriptive enough to guide daily actions, such as how to handle CUI, respond to security incidents, or conduct access reviews.
6. Incident Response and Reporting
Outline how incidents should be reported, documented, and escalated. Specify the roles responsible for responding to incidents and maintaining logs.
Include contact information for internal reporting and clear instructions on what constitutes an incident and the urgency of response.
7. Enforcement and Compliance
Explain how the policy will be enforced and monitored. State the potential consequences for non-compliance, which can range from corrective actions to termination, depending on the severity.
Consider including a framework for regular audits or reviews to ensure compliance.
8. References and Supporting Documents
List any relevant standards, regulations, or other internal policies (e.g., NIST 800-171, federal contractor guidelines) that align with or support the policy. This will help employees understand the broader compliance landscape and where the policy fits.
9. Training and Awareness Requirements
Specify any required training or awareness programs that employees must complete to understand and implement the policy correctly. Include the frequency of training (e.g., annual, quarterly) and any special certifications needed.
10. Policy Review and Updates
CMMC policies should be dynamic, evolving with new regulations and risks. Define a review cycle (e.g., annually) and identify who is responsible for reviewing and updating the policy.
Consider a process for documenting changes, which will help in demonstrating to auditors that policies are kept up-to-date.
11. Sign-off and Approval
A section for authorized signatures from executive leadership or cybersecurity officials, demonstrating that the policy has been reviewed and approved by upper management.
12. Documentation and Version Control
Include a version history that records changes, dates, and approvals. This is critical for demonstrating to CMMC assessors that your organization maintains a disciplined approach to policy management.
In creating CMMC policies, aim to keep language precise, actionable, and easy to understand across departments. Policies are most effective when they are not only compliant but integrated into the culture and operations of the organization.
If Policies Cover the “high level”, When would we Need to Develop a Procedure?
While policies lay out the high-level principles and rules, procedures provide the detailed roadmap needed to bring those policies to life. When an organization has established what needs to be done through a policy, a procedure serves as a companion document, offering step-by-step instructions on how to carry out specific tasks.

These procedures take the complexity of high-level goals and translate them into manageable actions, guiding employees through each phase of implementation to ensure accuracy and consistency.
Procedures Help to Prevent Errors
Procedures are essential in maintaining consistency across the organization, especially when multiple individuals or teams are responsible for similar tasks. By clearly outlining each step, procedures help prevent errors and omissions, creating a reliable process regardless of who performs it.
Consistency Contributes to a More Secure and Compliant Environment
This consistency not only safeguards the quality and integrity of the work but also contributes to a more secure and compliant environment by ensuring that critical tasks are completed thoroughly and correctly every time.
How Long Should Policies or Procedures Be?
-
- Policies and procedures need to be thorough enough to cover all necessary details but concise enough to be easily understood and followed.
- Avoid unnecessary information that can make the document cumbersome and difficult to follow.
- Focus on the most important points and streamline content to improve readability.
Additional Policy and Procedure Recommendations
Policy Document:
A typical policy document will have several pages and succinctly cover the key elements like purpose, scope, responsibility, etc.
It’s important to address your cybersecurity practices in detail and all NIST and CMMC requirements to the level of the assessment objectives.
The policy document can serve as a “cheat sheet” during the assessment.
Procedure Document:
The procedure document varies depending on complexity and can range from 3 to 10 pages focused on clear, step-by-step instructions.
How can we be sure Policies and Procedures Stay up to Date?
-
- Policies and procedures must be regularly reviewed and updated to remain relevant and effective.
- Regular reviews ensure that documentation reflects current practices, regulatory changes, and organizational needs.
- Establish a regular review cycle, typically annually or biannually, depending on the complexity and criticality of the document.
- Outline a clear process for updating documents, including steps for proposing changes, reviewing feedback, and approving revisions.
- Ensure updates are communicated to all relevant stakeholders and integrated into training programs.
- Encourage a culture of continuous improvement, where policies and procedures are regularly evaluated for effectiveness and efficiency.
Version Control and Tracking Changes
Version control is essential for keeping track of changes and ensuring that the most current version of a document is in use.
Use tools and software to track changes and manage document versions (e.g., document management systems, and version control software).
Ensure that all changes are documented, reviewed, and approved before being finalized.
Distribution of Updates:
Establish a process for distributing updated documents to all relevant stakeholders.
Ensure that old versions are archived and accessible for reference but clearly marked as outdated.
Access Control:
Limit editing rights to authorized personnel to prevent unauthorized changes.
What are some Time-Saving Strategies for Writing Policies and Procedures?
Use specialized templates
-
- Using templates can significantly reduce the time required to create policies and procedures from scratch.
- Templates provide a structured starting point and ensure consistency across documents.
- Customize templates to fit the specific needs and context of the organization.
Other Suggestions
-
- Schedule regular meetings and checkpoints to review progress and address any questions or concerns.
- Use document management systems (DMS) to create, store, and manage policies and procedures. DMS features like version control, access management, and collaboration tools enhance efficiency and accuracy.
What are some Policy and Procedures Mistakes and How can we Avoid them?
Lack of Clarity:
-
- Policies and procedures that are vague or ambiguous can lead to misunderstandings and inconsistent application.
- Avoid using jargon or overly complex language that may confuse readers.
Overly Lengthy Documents:
-
- Documents that are too long and detailed can be overwhelming and difficult to follow.
- Important information may get lost in excessively verbose descriptions.
Outdated Information:
-
- Failing to regularly update policies and procedures can result in outdated practices that do not reflect current regulations, technology, or organizational changes.
- Outdated documents can lead to non-compliance and security vulnerabilities.
Lack of Stakeholder Involvement:
-
- Not involving key stakeholders in the development and review process can result in incomplete or inaccurate documentation.
- Stakeholders may be unaware of or resistant to following policies and procedures they did not help create.
Poor Accessibility:
-
- If policies and procedures are not easily accessible to all relevant parties, they are unlikely to be followed consistently.
- Storing documents in hard-to-reach or poorly organized locations can hinder compliance.
Inconsistent Application:
-
- Inconsistent application of policies and procedures across different departments or teams can create confusion and gaps in security.
- Lack of standardization can lead to varied interpretations and implementations.
In Summary
In this webinar, we focused on the importance of documentation for your CMMC certification, and that policies and procedures are an essential starting point for preparing your cybersecurity program.
You should expect that your assessor will want to review these documents in detail. For those seeking further assistance, members of our consulting team are available to assist you.
We are happy to provide more information about our CORE Compliance Platform and the available policies, procedures, and other resources to help you prepare for CMMC certification.
About CORE Vault for NIST CMMC
Everything you need for NIST/CMMC in one cloud-based solution. The CORE Vault CUI Enclave and Consulting Services.
If you contract with the Department of Defense, you require advanced cybersecurity protections. To comply with DFARS, you need to meet the requirements of NIST SP 800-171. Soon, DoD contractors will also need to meet the requirements of Cybersecurity Maturity Model Certification (CMMC 2.0). However most contractors don’t have the resources to overhaul their entire network for compliance. With CORE Vault, you don’t have to.
With CORE Vault, you can separate government data from your network and access it through a secure, cloud-based environment managed by our cyber experts.
CORE Vault also includes the support needed to reach full compliance with the non-technical cybersecurity requirements, such as your system security plan and required policies.
We’ve seen contractors achieve their maximum DoD-required SPRS score in 30 days.

Core Business Solutions, established in 2000, is a Registered Practitioner Organization through the Cyber AB and has been providing consulting and technical solutions for NIST/CMMC for over 5 years. Rick Krick is the Director of Security Solutions for Core Business Solutions and directs our Cybersecurity Services solutions including CMMC. Rick has over 25 years of experience in Management System implementations, software development, IT services, and certifications.

